How Hashing Secures Blockchain Transactions
Hashing renders blockchain transactions secure by altering data into fixed-length codes that are unique, resilient, and securely verifiable. It facilitates digital signatures, preserves privacy, and enables virtual transfers to be trustworthy yet transparent.

In the realm of digital innovation, blockchain technology has risen as a groundbreaking force throughout various industries with its decentralized nature, transparency, and security features.
Blockchain technology has transformed how we process digital transactions by rendering them safer and fraud-resistant.
A fundamental aspect that makes blockchain secure is hashing. Thus, what is hashing, and in what way does it safeguard transactions on a blockchain?
Imagine a vast, unchangeable digital ledger where every transaction is permanently and securely recorded. Hashing is the element that allows this system to function, ensuring data remains unchangeable. It transforms data into a digital signature that confirms its authenticity.
In this guide, we aim to clarify what hashing entails, the process involved, and its crucial role in ensuring the security of blockchain transactions. We will maintain the ideas straightforwardly without sacrificing the foundational principles of this potent cryptographic method.
What is Hashing in Blockchain?
Hashing is a unidirectional method that takes any input (such as text, numbers, files, or transactions) and generates a string of characters of a specific length. A string(a hash) is specific to the input data. With a slight modification in the input, a completely different hash is produced.
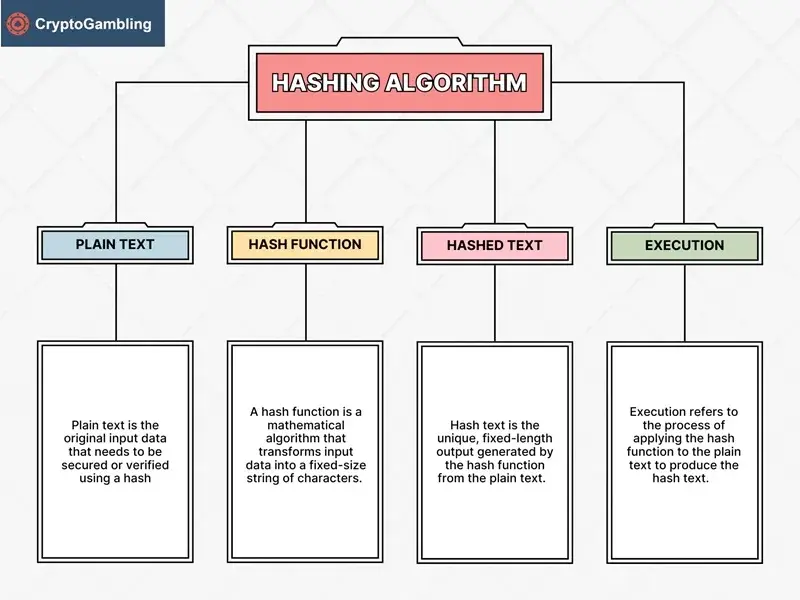 Let's say that hashing is a fingerprint of data. As no two human beings can have the same fingerprints, no two different inputs can share the same hash. This renders hashing an essential mechanism for preserving data integrity in blockchain networks.
Let's say that hashing is a fingerprint of data. As no two human beings can have the same fingerprints, no two different inputs can share the same hash. This renders hashing an essential mechanism for preserving data integrity in blockchain networks.
How Does Hashing Work?
A hash function accepts an input and generates an output of a predetermined size.
The prevalent hash function utilized in blockchain technology is SHA-256 (Secure Hash Algorithm 256-bit), which belongs to the SHA-2 group.
Here is an illustration of how SHA-256 works:
Output: "Blockchain is secure"
Hash Output: F2C7BFAB8F4F19B6C4D03A7259E60F9A4FBD946BFC9A2EDE2C11FDD8D93F5B06
If we alter only one letter, the hash changes entirely:
"blockchain is secure" (lowercase "b")
**Hash Output: ** D1E4E4B70C0E3561D204D9383F7A62A6501E1D1A1033EFC9D4D7E95EC99E0D98
This extreme alteration, referred to as the avalanche effect, guarantees that even a small alteration of the original data results in a completely different hash.
Why Hashing is Important in Blockchain?
Hashing ensures data integrity, secures transactions from tampering, and enables secure authentication. Bitcoin and Ethereum blockchain networks would be vulnerable to fraud, inefficiency, and tampering if hashing were not in place.
The following are the reasons why hashing is an important part of blockchain technology.
Preserving Data Integrity
One of the greatest advantages of blockchain is that it is unchangeable, i.e., once a transaction has been executed, it cannot be modified. Hashing plays an important role in making this property a reality.
Every block in a blockchain includes the hash of the previous block, linking them together in one unalterable chain.
If someone else tried to alter a transaction in one of the previous blocks by altering one number, this block's hash value will now be entirely different. Because every block is tied to the hash of the previous block, the alteration will make the entire chain unusable.
Moreover, blockchain networks are decentralized, so there will be another node in the network that will detect this change and discard it, thereby preventing fraud. Such a mechanism ensures that blockchain is tamper-proof and maintains data integrity.
Protecting Transactions Against Hacking and Fraud
Transactions can be forged or manipulated in conventional digital networks when a hacker takes over the system. Blockchain averts such a possibility with the application of cryptographic hashing.
Everything in a transaction in a blockchain is consolidated into a special hash or digital fingerprint. It is bundled with other transactions and sealed into a block. When the block is confirmed, its hash acts as a pointer for the subsequent block.
This cryptographically secure pointer guarantees that:
- Transactions can not be reversed or undone.
- Illegitimate transactions stand out clearly.
- The blockchain can be trusted with compromised nodes.
Enabling Safe and Fast Confirmation of Transactions
Blockchain is based on a proof-of-work (PoW) system where miners do the job of resolving cryptographic puzzles by calculating hashes.
Miners are required to discover a hash that fulfills certain levels of difficulty before appending a block to the chain. This guarantees that:
- Transactions are validated before being included in the blockchain.
- The network is decentralized and secure.
- It is computationally infeasible for the attackers to modify previous transactions.
Furthermore, hashing guarantees that only legitimate transactions are logged, and double-spending, along with other forms of monetary forgery, is impossible.
Preserving User Anonymity and Privacy
Personal data in conventional finance networks is kept in databases and server backups, which can be targeted and hacked.
Blockchain employs hashing to safeguard the users' identity by substituting sensitive information with cryptographic hashes.
For instance, rather than storing a user's name and account number, blockchain just stores the hashed version. Therefore, even if an attacker gains access to the blockchain, he/she will not be able to link transactions to actual-world identities.
Optimization of Storage and Scalability
Blockchain networks process millions of transactions, and storing raw transaction data would necessitate enormous storage.
Hashing reduces storage through the use of Merkle trees that enable effective verification of transactions only with the use of stored hashed values.
A Merkle tree is a data encryption structure used to manage data by sending those figures through a hashing algorithm in different ways to create a hash that represents all of the data in a file.
Merkle trees allow:
- Verification of transactions without keeping complete records.
- Minimizing the storage of node data.
- Enhanced transaction speed and scalability.
Hashing is essential to the security, efficiency, and credibility of blockchain - to authenticate transactions, prevent fraud, ensure privacy, and maximize storage.
How Does Hashing Secure Blockchain Digital Transactions?
Hashing keeps blockchain technology secure and ensures that there is no opacity whatsoever.
Preventing Data Manipulation
Blockchain transactions are immutable because they cannot be modified after being logged, which happens due to hashing.
If someone tries to change a specific transaction of a previous block, its hash will change and therefore break the link with the subsequent block and inform the whole network of the interference.
Since a blockchain is a decentralized system, in this case, others will discard the modified data, and thus, the network itself is safe.
Guaranteeing Safe Transaction Authentication
Miners confirm and authenticate a transaction before it is put into the blockchain, especially in Proof-of-Work blockchains like Bitcoin.
Miners now attempt to solve a cryptographic challenge in predicting a hash value that satisfies a particular difficulty requirement.
This whole process takes up computational resources and time, making it almost impossible for the attacker to alter the transactions.
When a miner arrives at the value of the hash, the block is added to the chain while the network authenticates the transaction.
Safeguarding User Privacy
The blockchain uses hashing in order to secure transactional data.
Instead of physically keeping personal data, actual information is replaced with hashed values on the blockchains to make it hard for hackers to obtain sensitive details.
For instance, if you transfer a Bitcoin to your friend, the transaction appears as such:
From: A17XH74B2C...
To: C9Z6K43V8D...
Amount: 0.5 BTC
Transaction Hash: B62E94A...
Because these identifiers have been hashed, it becomes quite difficult to track the true identities of the sender or receiver without supplementary knowledge.
Activating Digital Signatures
Hashing aids in the function of digital signatures, which serve to validate the authenticity of transactions.
Each user holds a private key accompanied by a public key. Whenever you approve a transaction, your private key will generate a hashed signature and establish that you are the rightful owner of the assets.
The other members of the network, however, can use your public key to verify your signature and thus prove the validity of the transaction.
Enabling Effective Data Storage
Rather than maintaining complete transaction histories, blockchain systems utilize Merkle trees designed to preserve your personal information in the form of hashes only.
This saves storage space and provides a mechanism for rendering faster transaction validation, thus making blockchain systems more efficient.
Real-World Example: Bitcoin’s Use of Hashing
Hashing is crucial to the security of Bitcoin, the first and most well-known cryptocurrency in the world.
Because:
- The blockchain records and hashes each Bitcoin transaction.
- Before adding a new block, miners must find a hash that meets the network's difficulty target.
- Attacks are avoided because the blockchain with the longest chain of hashes is regarded as legitimate.
Bitcoin's decentralized, trustless system would not function without hashing.
Is Hashing Perfect? Challenges and Limitations
Although hashing is a key component of blockchain security, it is not without flaws.
Hashing has its own set of difficulties and restrictions, even if it offers data protection, immutability, and integrity.
Let's examine a few of the main issues:
Pre-Image Attacks (Reverse Engineering a Hash)
One of the biggest theoretical risks in hashing is the pre-image attack. This occurs when a hacker attempts to decipher a hash in order to find the original input.
Typically, hash functions such as SHA-256 are usually intended to be one-way. They take an input and produce a fixed-length hash, but the aim is that the hash makes it difficult to determine the original input.
But as computational power increases, particularly with quantum computing on the horizon, there is a chance that attackers will someday be able to brute-force their way to the original data. Blockchain transaction security may be at risk if a hashing algorithm is made vulnerable to pre-image attacks.
Solution
Researchers are actively developing quantum-resistant hash functions that would make pre-image attacks nearly impossible, even with the most powerful computers.
Collision Resistance (Two Different Inputs Producing the Same Hash)
A collision occurs when two distinct inputs yield the same hash output. Ideally, a perfect hash function would mostly prevent these kinds of problems from happening.
However, the number of possible hash numbers is lower, as hash functions generate a fixed number of output bits. Although it is only in very rare cases that two different inputs can create the same hash, and this situation is termed a hash collision.
This is a critical issue for the security of blockchains as they make use of hashes in order to be able to carry out transaction validation.
In instances where a hacker can find two different transactions producing the same hash, it is possible for them to manipulate the system in accepting a fraudulent transaction.
Real-World Example
-
The MD5 hashing algorithm, which is a gem of an old vintage, was found to be affected by collisions, and hence, it became a keystone unfit for secure environments.
-
Consequently, more secure algorithms like SHA-256 and SHA-3 are now the go-to choices in blockchain technology.
Solution
-
Modern blockchains employ lengthier and more intricate hashing algorithms, such as SHA-256 and SHA-3, to lower the danger of hash collisions.
-
Moreover, blockchain algorithms have an enormous number of possible hash outputs, making collisions highly uncommon.
Energy Consumption and Computational Costs
The most significant complaint about blockchain security, especially in the case of Proof-of-Work (PoW) blockchains like Bitcoin, is the amount of energy that is being used for hashing.
Miners have to solve complex cryptographic puzzles by hashing different inputs repeatedly until they find a hash that meets the network’s difficulty requirements. This mining process is a resource-intensive operation that requires robust computational power and consumes a large amount of electricity.
Real-World Impact
-
The electricity that the Bitcoin network uses alone is as much as the energy used by huge countries such as Argentina or the Netherlands.
-
Critics claim that blockchain mining activities are a cause of environmental problems because of the high levels of energy consumption and carbon emissions.
Solution
-
Alternative consensus methods, such as Proof-of-Stake (PoS) and Delegated Proof-of-Stake (DPoS,) considerably decrease the amount of power needed by eliminating the necessity for competitive mining. Consequently, some of the blockchains, as Ethereum, have moved from the Proof-of-Work method to the Proof-of-Stake one to secure the energy of blockchain technology and improve the ecology of the planet.
Vulnerability to Quantum Computing
Contrary to traditional machines, which would need a significant amount of time to crack a hash function, quantum computers would be able to finish the task in much less time.
Quantum computers function with qubits rather than regular digital bits, which allows them to conduct calculations substantially faster.
The result is that by using only a quantum computer, one is able to hash SHA-256 very fast, which in turn makes the traditional blockchain security method completely outmoded.
A Possibility
We would reach the point where a quantum computer can recover private keys from public ones and, hence, compromise your cryptocurrency wallets. Plus, quantum attacks may enable an attacker to rewrite the blockchain’s hierarchical data, thereby causing decentralized networks to lose their standing.
Solution
- Experts are now in the process of coming up with such cryptographic algorithms that will be quantum-resistant, e.g., NIST's SHA-3 and the post-quantum cryptography for the purpose of blockchain security.
- There are some projects that are progressing on blockchain technology and are trying to use hybrid cryptography, going from classical to quantum-resistant techniques.
Dependence on Hashing Standards
The security of blockchain is closely related to the robustness of the algorithms in the hashing process, like SHA-256, for instance.
Needless to say, with the development of technology, even this older method of keeping the system secure can become out of date.
If a hashing algorithm that is overwhelmingly used is exposed, the advancement of entire blockchain networks could be at risk.
Solution
-
To avoid the situations described, blockchain developers need to keep changing the hashing algorithms to stronger ones over time. For example, Bitcoin might change its hashing algorithm to SHA-3 or a hash method that is not affected by a quantum computer when and if SHA-256 gets compromised.
-
On the other hand, new blockchains might employ quantum-resistant hash functions from the earliest stages of their release.
While the limitations still exist, the continuous progress in cryptographic research, the development of quantum-resistant algorithms, and energy-efficient consensus mechanisms may ensure that these issues will be resolved and that blockchain technology will remain secure and safe in the future.
Future of Hashing in Blockchain Security
Hashing will continue to be a crucial component in the security of blockchain technology as it keeps evolving.
Nevertheless, the future of blockchain technology is being affected by the new developments and challenges impelling it.
Quantum-Resistant Hashing
The increasing use of quantum computing is seen as one of the major threats to blockchain security. That is because quantum computers are able to solve tough mathematical problems at a rate of growth that is truly unfathomable.
The implication is that there is a risk that quantum computers running the SHA-256 algorithm will disrupt the operations of blockchain networks.
As a solution, industry professionals are implementing quantum-resistant hash functions, such as the SHA-3 family ones or lattice-based cryptography, to shield themselves against future threats.
More Energy-Efficient Hashing
Blockchain networks based on the Proof-of-Work (PoW) consensus mechanism are currently in high demand for the computational power they need to fight off cryptographic attacks.
The new generation of hashing algorithms is geared at reducing the amount of power consumption but still upholding security.
Some of these techniques include Proof-of-Stake (PoS), Proof-of-Space (PoSp), and sharding to supplement hashing, thus making blockchains more sustainable.
Hybrid Cryptographic Techniques
Cryptographers are looking into methods that are capable of mixing cryptographic methods to get the most secure method.
The blockchain of the future may include hashing, zero-knowledge proofs, and homomorphic encryption for transaction security and the enhancement of privacy and efficiency.
AI-Powered Hashing Security
The use of advanced artificial intelligence technology is what might be expected to be an era of the most successful and secure hashing algorithms.
AI will be able to notice any form of abnormality, threat, or security loophole in advance, thereby enhancing the security of blockchain.
The new features will guarantee that the process of hashing for blockchain is a robust, safe, and productive pathway in the future.
Final Words
Hashing is the very basis of blockchain security. It guarantees that the data stays the same, verifies the transaction, and provides resistance to fraud.
In the absence of hashing, the whole cryptocurrency network, like Bitcoin and Ethereu,m would be at risk of being attacked.
By turning the data into unique and unchangeable fingerprints that are the source of trust, hash power makes blockchain transactions secure, transparent, and immutable.
The adoption of the blockchain continues to expand, and hashing will still be used to protect digital assets, smart contracts, and DApps, and consequently will form the pillars of the digital transaction world.
Furthermore, for any person interested in blockchain, cryptocurrency, or cybersecurity, visit CryptoGambling, the most well-detailed crypto blog and game site.














