Top Security Tips and Proven Strategies to Protect Your Cryptocurrency
Keep your crypto safe! Use strong passwords, enable 2FA, store assets in hardware wallets, stay sharp against phishing, use VPNs on public Wi-Fi, and keep your software updated. Stay smart, stay secure, and outsmart hackers in the digital world!

The amount of funds stolen from the cryptocurrency platform in 2024 rose by about 21.07% year-over-year (YoY) to $2.2 billion, and there were 303 hacking incidents in 2024 compared to 282 in 2023.
Cryptocurrencies have been disruptive and have changed the way we view and perceive money. As a result, more and more people are using cryptocurrency as a means of payment and or investment. Although crypto, which uses blockchain technology, is one of the safest security measures for your assets in modern times, we cannot rule out the risks of handling these digital assets.
Moreover, keeping yourself updated about security tips is essential as hackers and scammers are always on the lookout for your e-money. You can have the best wallet and implement the best measures to protect your digital money, but one mistake and it can all be gone.
For instance, purchasing other assets like NFTs with cryptocurrency or crypto casinos and gambling is getting more popular and requires frequent transactions. If you share your credentials with someone or just download a crypto wallet from a random site, you risk losing all the blockchain assets.
This blog is not about the risks and challenges of crypto currency, but it's the total opposite. This blog is a comprehensive guide on how you can protect your crypto money with the top security and safety tips and proven strategies.
What is Cryptocurrency?
Cryptocurrency refers to a sort of digital and decentralized currency that has limited supply. This digital currency uses cryptographic techniques for security. These currencies function on smart contracts based on blockchain technology and do not require intermediaries and regulatory bodies for transactions.
Cryptocurrencies function on decentralized networks built on blockchain technology, which means it is totally different from the traditional fiat currencies that are issued and controlled by central banks (like the US dollar or the euro). Some of the best examples of cryptocurrencies include Bitcoin and Ethereum.
Use Strong Password
The first security measure is to use a strong password. This may sound too common, but you should be well aware of how using the same passwords everywhere or using simple codes can lead to hacking and unauthorized access to your assets. So, you need to create a strong and unique password for your wallet and devices that contain information about your digital assets. This can be essential to avoid your accounts being vulnerable to hacking attempts.
One strong recommendation is to avoid using easily guessable details like your name, birthday, or favourite sports team.
This measure is quite relevant if you are crypto trading, purchasing NFTs or engaging in crypto gambling. This is because there is a higher number of transactions during this process. So, always use different passwords for each account. Consider using a password manager to generate and store complex passwords securely.
Enable Two-Factor Authentication (2FA)
Next, we have two-factor authentication (2FA,) which is one of the highly proven strategies for crypto security. Most of the digital wallets and software applications already have a 2FA built up in their system. However, there is a chance that your digital vault or storage does not have this safety measure. In such cases, ensure you integrate safe software for your protection.
2FA implies that, even when a hacker gets your password, their attempt will fail without the second layer of security given by 2FA. Most virtual currency platforms offering services related to trading and gaming support 2FA options.
Furthermore, the 2FA's need is rising in the current market. For instance, Top crypto gambling platforms demand this security feature as these sites often store private keys or provide access to substantial amounts of digital funds. So, you are suggested to choose authenticator apps over (Short Message Service) SMS-based 2FA for increased security, as SMS can be vulnerable to SIM (Subscriber Identity Module) swapping attacks.
Use Hardware Wallets for Storing Crypto

There are two kinds of crypto wallets available in the market. One is warm wallets or online storage, and the other is cold wallets or offline storage.
While online wallets and exchange are in place for convenience, their use puts your assets in the way of possible hacking or phishing. Store your long-term cryptocurrency in a hardware wallet: a physical device that keeps keys offline and away from prying hacker eyes. So, if you are storing your assets for a long time and do not require frequent translation, always use a hardware wallet for cryptocurrency security.
There is another kind of wallet called a paper wallet. However, they are prone to damage and are not recommended much.
Be Cautious of Phishing Attacks
Phishing attacks have been a huge headache for the public since the use of digital tools and assets. Hackers and scammers alike are always looking for new ways to steal your hard-earned assets from cryptocurrency market. So, you need to be careful about everything that seems suspicious.
Scammers create fake websites or send fraudulent emails in an attempt to steal your login details or private keys.
Always double-check the URL before entering sensitive information, and never click on links from unsolicited emails. There is a chance that you will get an email promising a bonus for downloading an app. Likewise, if some offer from a gambling site promises hugely lucrative returns or bonuses, be extra careful, as it can be phishing. Check if the email and the gambling sites are authentic or not.
Furthermore, never download and install applications, software and updates on your device from unknown sites.
Keep Software Up to Date
If you are among the millions of people who just click “Skip” in application or device updates, it might be a good time to stop doing that. That’s, of course, if you want to keep your assets safe. The Skip button seems tempting as the updates usually take a long time to finish. Who has that time, right? Well, you need to have that time.
Crypto-related applications and software are in a constant state of development, and updating them means you will benefit from the latest security features and bug fixes. Older versions of any software may contain vulnerabilities that hackers can exploit. So, make sure to update whenever possible.
Use VPNs for Extra Privacy and Security
A VPN helps you hide your personal information, making you safer from hackers online. Encryption through a VPN adds a layer of security by encrypting your internet connection. This is important, especially when performing cryptocurrency transaction because it blocks hackers' interception of data on unsecured networks.
Public Wi-Fi hotspots, such as those in cafes or airports, are highly vulnerable to cyberattacks. We suggest you use mobile data if you are making payments or using online transactions. However, if you need to use public wifi, always connect to a VPN first.
A VPN ensures that your browsing activity, including crypto transactions, is kept private and secure. Choose a reliable VPN provider to enhance your online privacy and protect your crypto assets from potential threats.
Backup Your Private Keys Securely
The private key is the most important data of virtual currency. Private keys enable one to have access to their money and any other transaction they want. A lost private key, either through misplacement or theft, simply means your digital assets are gone.
So, always back up your private keys securely. Write them on paper and store them in a safe, offline place or on an encrypted USB. Never store private keys digitally without encryption; otherwise, when your device is compromised, it will expose them to theft.
Be Mindful of Social Engineering Scams
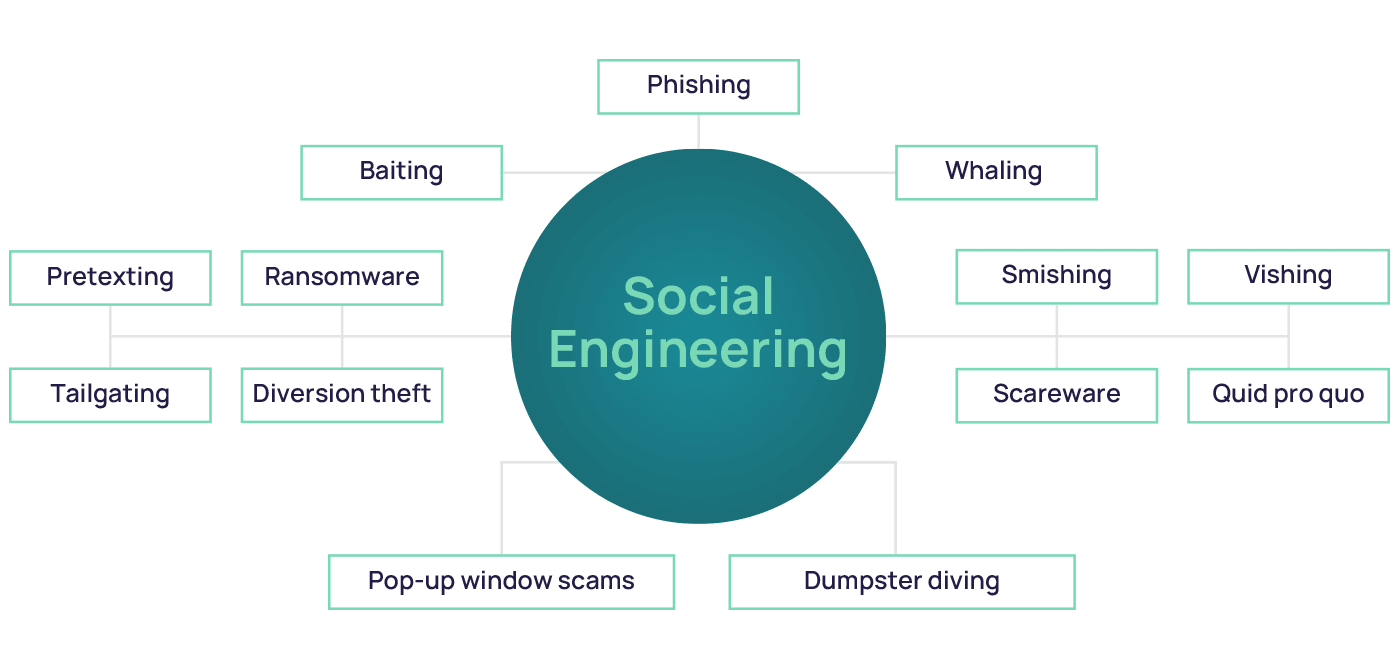
Social engineering scams are one-way hackers manipulate individuals into giving them inside information. These could be in the form of fake calls, emails, or messages from apparently very trusted sources. This is quite similar to phishing but much more dangerous as a social engineering scam is less suspicious.
Always be wary when anyone contacts you and asks for your private information, especially about your digital currency accounts. No reputable company would ever request your private keys or credentials to log in. If you are in doubt, always verify such requests through official channels before taking any action.
Monitor Account Activity Regularly
Regular monitoring of your cryptocurrency accounts is important to try and catch unauthorized access or suspicious activity. Most exchanges and wallets have alerts when attempts at log in, transactions, and withdrawals occur.
Paying close attention to your accounts will help you instantly identify if an intruder has accessed your assets and do everything in your power to contain it. Set up alerts with major activities, like withdrawals or changes in your account details, to keep yourself updated.
Stay Informed About the Latest Security Threats
The world of cryptocurrency is constantly changing, as are the security threats that accompany it. Being up to date with the latest security vulnerabilities and scams is one of the best ways to take care of your crypto assets and protect your investing in cryptocurrency.
Follow the news in the crypto world concerning security issues and be able to react on time in case of new threats. Keep up with recent news about the emergence of some scams, phishing, or other vulnerabilities to modify your cryptographic assets in time.
Use Multi-Signature Wallets for Enhanced Security
Always use a multi-signature wallet if possible. This storage requires several private keys in order to perform one transaction, adding an extra layer of security. For example, in a 2-of-3 wallet, two out of three keys are required to complete a transaction, making it harder for hackers to steal funds.
Such wallets are great for storing big amounts of cryptocurrency or business-oriented funds. Among the services which may be trusted, some provide multi-sig options: Electrum, BitGo, and Coinbase Custody.
Why You Should Consider Multi-Signature Wallets
The secure management of cryptocurrency assets finds its ideal solution through multi-signature wallets. A multi-signature wallet needs several different private keys to validate transactions because it differs from simple private key-controlled digital wallets.
The additional security protection becomes essential specifically for people and organizations that handle substantial cryptocurrency amounts. Several required approval steps enable substantial protection against unauthorized access or private key loss through security breaches.

Multi-signature wallets establish their primary value through reinforced security measures for wallet protection. The increasing number of hacking and fraudulent threats within cryptocurrency territory makes it dangerous to depend on a single private key as the sole point of authentication.
A multi-signature wallet system needs three valid signatures from five possible signatures to execute transactions. The multi-key system protects financial assets from key breaches and requires collective agreement from all parties to authorize transactions, thus promoting collaborative asset management.
Multi-signature wallets establish operational oversight while simultaneously providing accountability to wallet management operations. The system provides exceptional benefits for organizations that handle financial resources through various staff members.
A team-based control structure incorporated into multi-signature wallets enables better financial transparency throughout the processes of decision-making and transaction management. The team shares responsibility for every transaction which minimizes internal fraud incidents and increases their capacity to track and audit transactions properly.
Using multi-signature wallets is a secure decision for cryptocurrency management in current times. Multi-signature wallets deliver better security, rational transparency, and enhanced accountability, which traditional digital wallets cannot match.
The adoption of multi-signature solutions has become fundamental for secure crypto asset management since organizations and people understand digital asset protection's value.
How Hardware Security Modules Protect Your Crypto
Digital currencies make Hardware Security Modules (HSMs) essential to protect keys effectively because hardware is effective at protecting keys. Special-purpose security hardware is used to securely store crypto-sensitive operations in separated operation areas and to manage cryptography keys in separated working areas. Hardware Security Modules have primary encrypting functions that protect private keys while they move over networks.
HSMs protect private keys through their capability to quarantine them against possible security threats in servers and applications. The HSM offers protection to private keys in a way such that thieves cannot steal it even if they make unauthorized access to servers used to host wallets.
HSM security level relies on several factors of authentication that combine password security with physical tokens or biometric scanning. The stringent access control of keys secures cryptocurrency assets through enabling users who have authority to access it to manage it thus minimizing possible unauthorized access and malware threats.
Secure multi-party computation is more important in complex cryptocurrency environments because HSMs provide it as a function. Secret splitting and built-in HSM threshold signing prevent a single user's control over transactions. HSM security benefits come in handy in business and institutional crypto portfolio management because they protect openness and safety in sensitive financial transactions.
Access by malicious actors would lead them to encounter encrypted data but the information remains unreadable to them. The tamper-resistant capabilities of HSMs strengthen their security capabilities. These devices contain an automatic destruction capability which triggers when unauthorized access attempts to protect the cryptographic keys stored inside them thus maintaining asset security.
Through HSMs multiple stakeholders can join crypto management activities because they share responsibilities to protect their digital assets.
The implementation of HSMs enables cryptocurrency businesses to meet enhanced regulatory requirements which become more stringent because of government interventions in digital assets. HSMs enable crypto businesses to satisfy AML and KYC requirements through their detailed logging systems which track key operational events.
Built-in compliance features on HSMs protect cryptocurrency businesses from legal problems and establish trust with users which makes them essential components of contemporary crypto security practices. People seeking top-level security for their digital assets need to adopt HSMs as their fundamental protection mechanism.
Conclusion
With the growing popularity of cryptocurrencies, digital asset security has become very important day by day. In such a case, where the frequency and magnitude of hacks and scams are rising each day, one must make sure to be well ahead in the game.
Security, however, is not a one-time fix; it requires constant vigilance in the form of staying updated on new threats and monitoring your accounts on a regular basis. By being proactive and following best practices, you will be able to keep your cryptocurrency safe in this ever-changing digital space.
Your digital wealth is ultimately your responsibility, and you can have all the benefits of digital currency without giving away your security if you take the necessary precautions.
Some common questions
What is the best way to protect my cryptocurrency?
Here are the best ways to protect your digital currency;
- Using a combination of strong passwords.
- Enabling two-factor authentication (2FA).
- Storing your assets in secure wallets such as hardware wallets.
- Regularly updating software.
- Using VPNs.
Why would a hardware wallet be used for long-term storage?
Hardware wallets are considered a very secure option for the long-term storage of virtual currency, as they keep your private keys offline. Hence, they become less vulnerable to hacks and phishing compared with hot or online wallets.
What is two-factor authentication (2FA), and why is it important?
2FA is a high level of security that verifies a login to an account with two different forms of verification; for example, a password and a code sent to your phone. This is pretty important for virtual currency accounts because it will make any form of access by hackers truly difficult, even with the knowledge of your password.
How can I recognize a phishing attack?
Most phishing happens through fake websites, emails, or messages that will try to steal your login credentials or private keys. Always check URLs for correctness and whether you are on the correct website before filling in sensitive information. Be wary of unsolicited emails promising bonuses or urgent requests for your details.
Can I use SMS for 2FA?
While SMS-based 2FA is better than none, it is vulnerable to attacks such as SIM swapping. It's highly recommended that authenticator apps-like like Google Authenticator Offer far superior security compared to any SMS-based alternatives.
What's a multisig, and why do I have to use one?
A multi-signature wallet requires multiple private keys to authorize a transaction, an extra layer of added security. It is very useful for large volumes of cryptocurrency or business-related funds, given that it is going to keep away unauthorized access and require approval by more than one party.
A multi-signature wallet requires multiple private keys to authorize a transaction, an extra layer of added security. It is very useful for large volumes of cryptocurrency or business-related funds, given that it is going to keep away unauthorized access and require approval by more than one party.
Is it safe to use public Wi-Fi and deal in cryptocurrency?
Public Wi-Fi networks are not secure and are considered to be targeted by cyberattacks. If you must use public Wi-Fi, ensure the addition of a trusted VPN to encrypt your connection and keep sensitive data safe from interception.
How can I safely back up my Crypto private keys?
Private keys should never be stored digitally without encryption. They should, instead, be written down and kept in a safe, offline location, such as a secure paper wallet or encrypted USB drive, to protect against unauthorized access.
How do I stay updated with the latest on security threats affecting cryptocurrencies?
Keep up to date with well-known crypto news feeds, blogs, and security forums. Most of the exchanges and wallet providers have security alerts and vulnerability updates, too. This will help you monitor emerging scams and hacks, thus taking timely action to secure your assets.














